In this case study, we’ll take a look at E-Corporation, which has recently implemented an analytic solution within the SAP HANA platform.
Overview
The company has provisioned tables; loaded data with an extract, transform, and load (ETL) tool; and created a series of SAP HANA information views. The user community will primarily interact with the SAP HANA information views, which will be secured with an analytic privilege that limits data access by region. Each user will have her own logon to the SAP HANA system to accommodate the data security requirements. However, users will primarily access the data via SAP BusinessObjects Business Intelligence (BI). The SAP BusinessObjects BI system has been configured to support single sign-on (SSO) for the SAP HANA platform with Security Assertion Markup Language (SAML) authentication.
In addition to the privileges needed to secure access to the information views, the security model must support power user access, developer access, and security administrator access.
E-Corporation has contacted its lead SAP HANA security consultant and requested help in defining a security model to accommodate its security requirements. The consultant has determined that a series of repository roles will need to be defined. Let’s look further at the consultant’s decision-making process and the four repository roles recommended for this project.
Consumer Repository Role
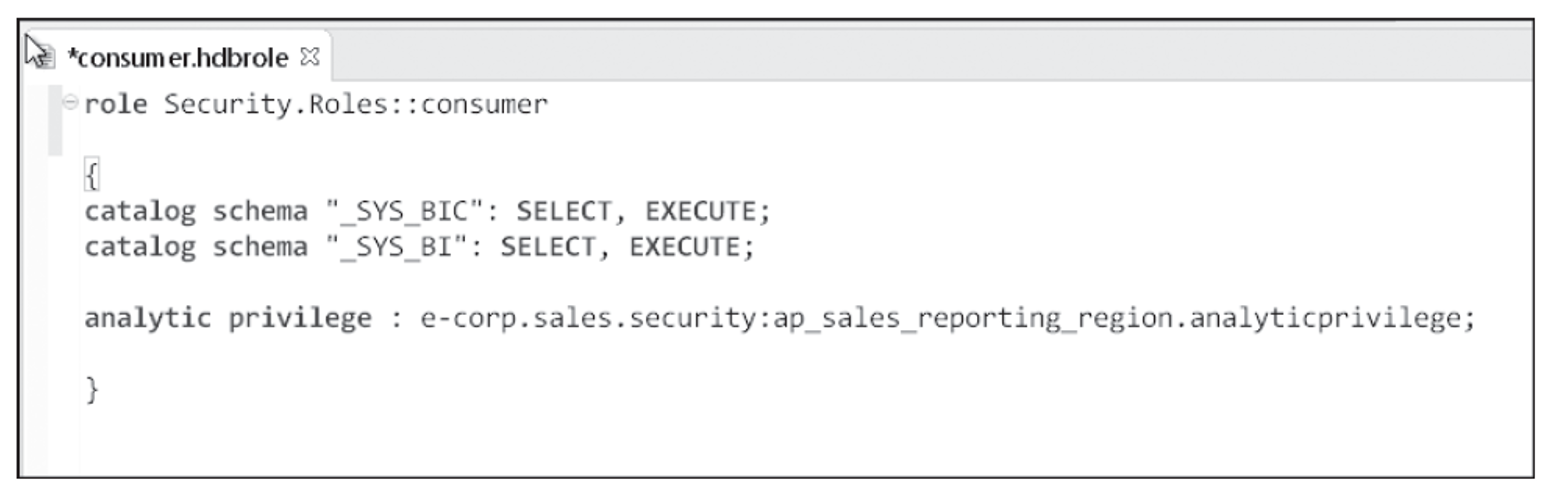
The first repository role will provide a base level of access to SAP HANA information views. The name of the repository role will be consumer. This role will grant SELECT and EXECUTE access to the _SYS_BI schema, which is required because additional metadata is published to this schema. The role will also grant SELECT access to the design time calculation view e-corp.sales.models::SCV_CUSTOMER_SALES. Users will need to have SELECT access, at a minimum, to query the information views and metadata in the _SYS_BIC schema.
When you reference the design-time calculation view in the repository role, the system will automatically grant access to its corresponding column view in the _SYS_BIC schema. An analytic privilege will also be granted. The analytic privileges will limit the consumer’s access to a series of information views and will dynamically filter the results of the views so that each user will be limited to one or more sales regions based on his predetermined security profile.
Data consumers also need access to the SAP HANA Info Access service hosted in the SAP HANA XS platform. To use this service, these users are granted the role sap.bc.ina.service.v2.userRole::INA_USER. In addition, some consumers need the ability to change their passwords using a web interface hosted in the SAP HANA XS platform. The role sap.hana.xs.formLogin.profile::ProfileOwner must be granted to allow consumers access to this utility.
The figure below shows the configuration of the consumer repository role script, which in our example, contains two catalog schema privileges and one analytic privilege.
Power User Repository Role
In addition to the standard users at E-Corporation, a small group of power users require unique permissions. These users need access the SAP HANA Web-Based Development Workbench to query information views and tables for debugging purposes. They’ll also need to access the SAP HANA packages to view the design-time versions of the SAP HANA information views. Therefore, they’ll need basic access to the SAP HANA repository. To accommodate this requirement, the security consultant recommends that an additional repository role named poweruser be created.
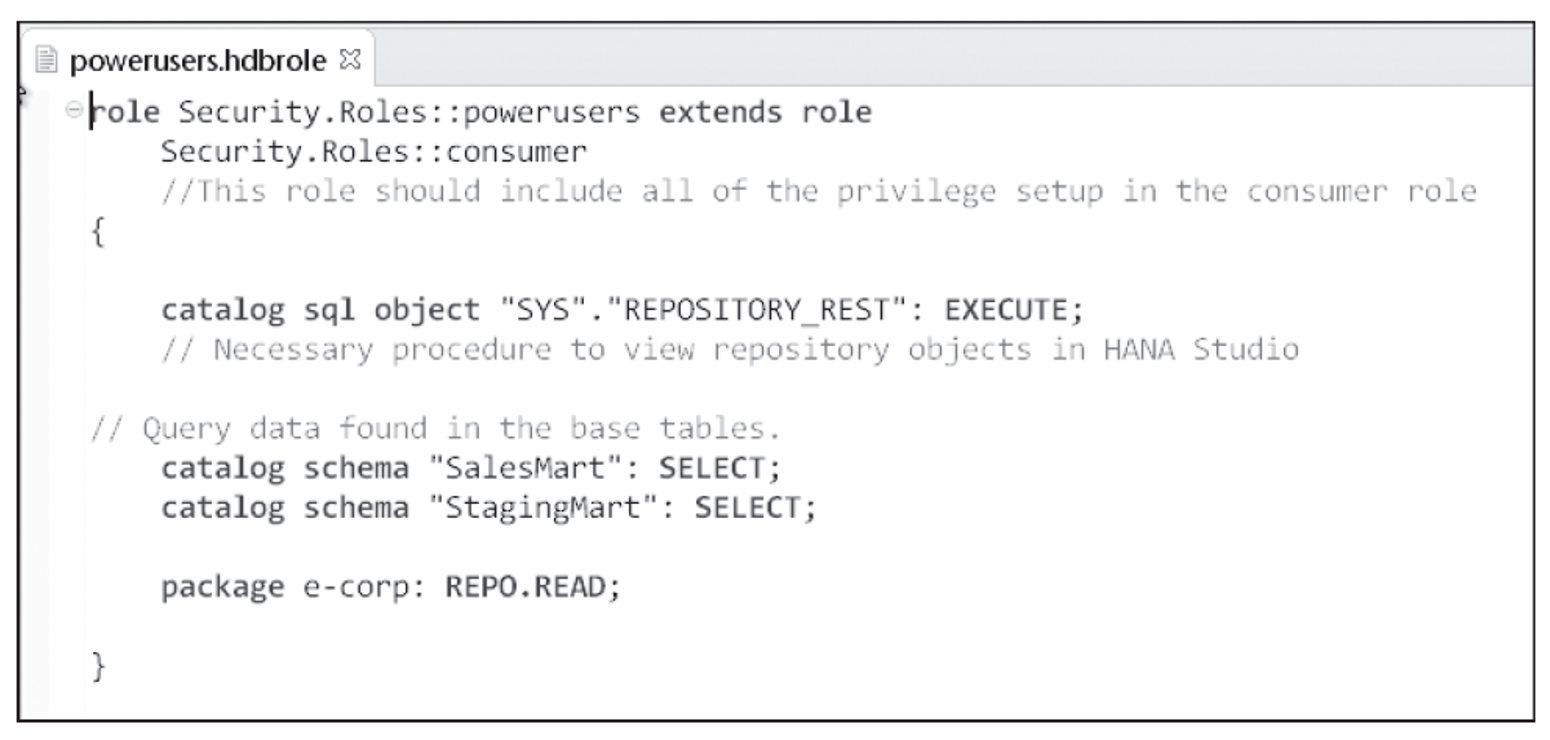
The poweruser repository role will be an extension of the consumer repository role, which means that power users will inherit all the privileges assigned to the consumer repository role. The poweruser repository role will grant access to the REPOSITORY_REST stored procedure, which is required to access the package hierarchy within SAP HANA. It will also grant SELECT access to the schemas housing the data used by the SAP HANA information views. Finally, it will grant REPO.READ access to the e-corp package, which will allow a power user the ability to view the configuration of each information view within the repository.
Below shows the configuration of the poweruser repository role script, which contains all the privileges necessary to accommodate the security requirements.
Developer Repository Role
The developers at E-Corporation will require access to SAP HANA and the SAP HANA Web-Based Development Workbench. These users will be responsible for creating the development artifacts used by the analytic solution. At a high level, developers require the following privileges and accesses:
- Developers will require at least the privileges assigned to the consumer and power user repository roles.
- Developers need the ability to fully manage the staging and data mart schemas. They’ll also be responsible for creating and managing the tables used by the solution.
- Developers will require access to the SAP HANA repository, system views, SAP HANA application lifecycle management, delivery units, analytic privileges, and import and export interfaces.
- Developers will require access to all data when querying SAP HANA information views.
- Developers will require full access to the e-corp package and its child packages.
- Developers will require read access to all packages and development artifacts.
- Developers will require access to the SAP HANA Web-Based Development Workbench.
To accommodate these requirements, a repository role named developer will be created. The next figure shows the repository role script designed to accommodate E-Corporation’s requirements for developers.
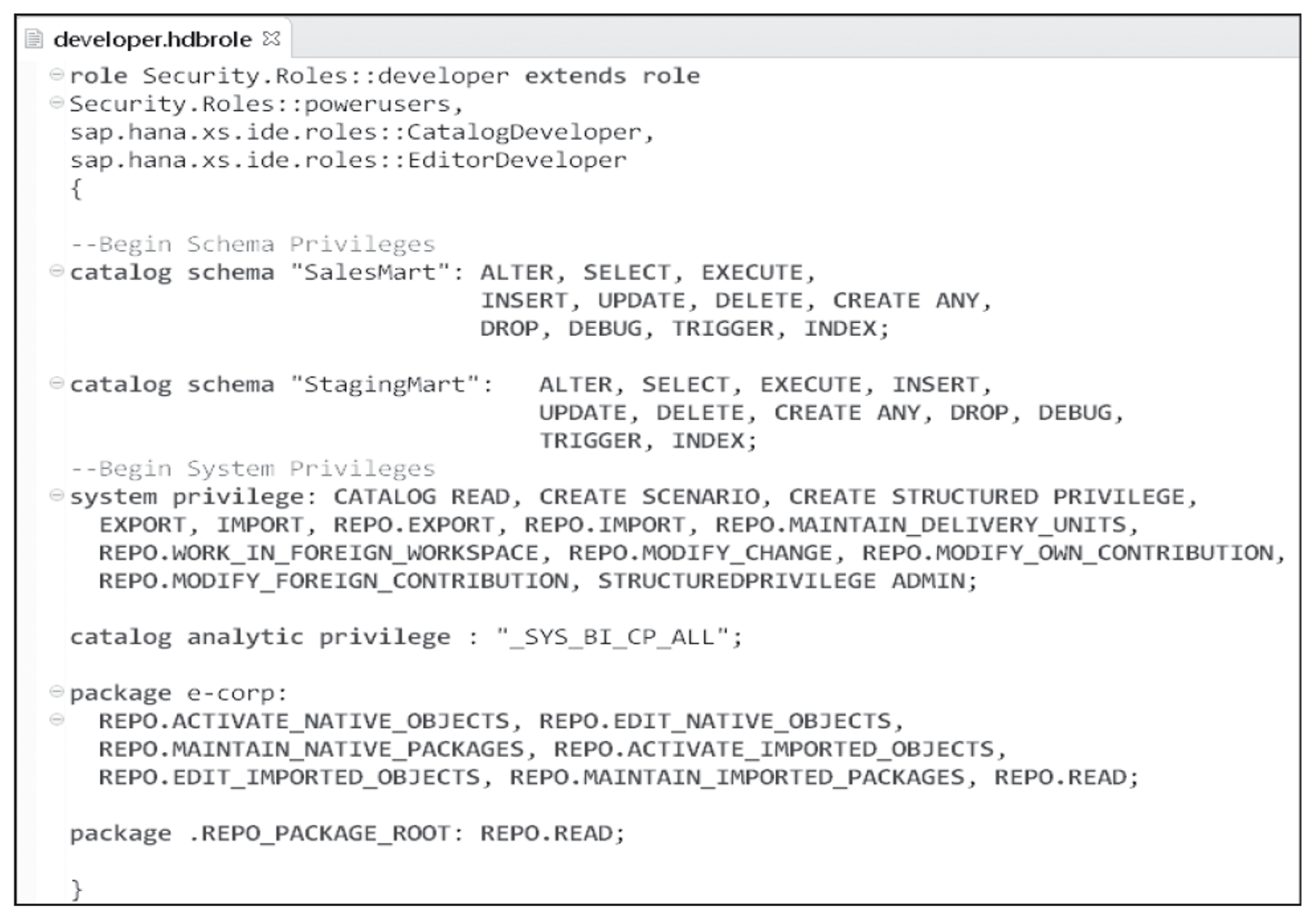
Let’s look at how the developer repository role script shown above fulfills the requirements:
- By including three existing roles within the extends role section of the script, two requirements are achieved. Developers will gain all the privileges of the consumer and poweruser roles and will gain access to the SAP HANA Web-Based Development Workbench.
- The two schema privilege lines grant the role full access to the staging and data mart schemas using their design-time reference.
- The items listed in the system privilege line grant access to the SAP HANA repository, system views, SAP HANA application lifecycle management, delivery units, analytic privileges, and import and export interfaces.
- The catalog analytic privilege line grants full query access to all SAP HANA information views.
- The first package line grants full access to the top-level e-corp
- The second package line grants read-only access to the entire package hierarchy.
As you can see, developer requirements can be fulfilled by including a few existing roles and by specifying several specific privileges. Referencing existing roles is helpful by reducing redundancy within custom repository roles. These references also ensure that the developer role will inherit the same privileges as the lower-level power user and consumer roles. Two of the existing repository roles also provided application privileges specific to the SAP HANA Web-Based Development Workbench.
Security Administrator Repository Role
The final recommended repository role grants privileges to a select group of security administrators. This role must provide security administrators the ability to manage users, create repository roles, and grant permissions. The following figure shows the privileges and additional roles that will be assigned to the repository role named SecurityAdmin.
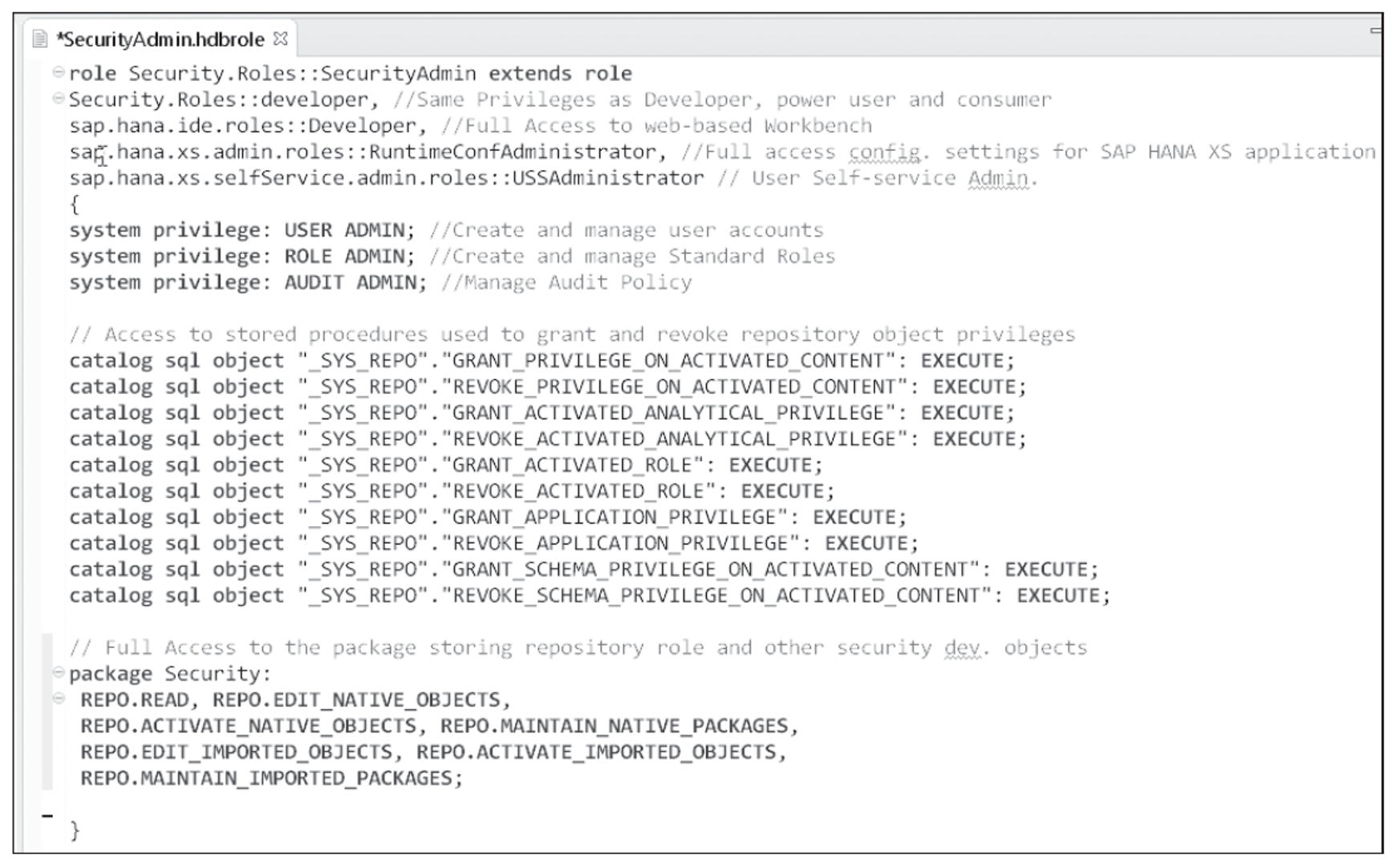
As described in the comments within the script, the security administrator role is an extension of the developer role and three additional XS engine application-specific roles. The applications in the XS engine provide interfaces useful in managing a security model. Three additional system privilege lines are included to grant user, role, and audit management. The catalog sql object lines grant EXECUTE privileges for a series of stored procedures necessary to grant and revoke privileges for objects owned by _SYS_REPO. Finally, the package security lines are included to provide exclusive access to the top-level package that will be used to store security-related development artifacts.
Conclusion
Once the repository roles are activated and assigned to the appropriate users, E-Corporation will have the makings of a sound security model. Because the company used repository roles, the model can easily be transported to other systems and managed using lifecycle management best practices. In addition, the _SYS_REPO system account will be the primary owner and grantor of the privileges.
To learn more about granting object privileges with repository roles, check out this post.
Editor’s note: This post has been adapted from a section of the book SAP HANA 2.0 Security Guide by Jonathan Haun.



Comments