After the initial user authentication on an ABAP server, an HTTP security session is established between the client (web browser) and the server (ABAP system).
Because HTTP is a stateless protocol, implying each request (GET) and response (POST) pair is independent from other web interactions, it’s important to implement HTTP security session management. In SAP systems, this is done using Transaction SICF_SESSIONS.
Service Component Port Number
After an authenticated session is established, the session ID (or token) is transferred between the client and the server. The session ID binds the user authentication credentials and the appropriate access controls enforced by the web application. The session ID can be exchanged using the host-specific, non-persistent session cookies. The cookie attributes can be used to add extra layers of security during exchange of the session ID. The two major attributes are as follows.
Secure Attribute
This attribute allows the web browsers to only send the cookie through an encrypted HTTPS (SSL/TLS) connection. This helps in preventing the man-in-the-middle attacks by ensuring that the session ID isn’t disclosed during the exchange mechanism.
HttpOnly Attribute
This attribute helps protect the confidentiality of the cookie by instructing web browsers to not allow access to cookies via the Document Object Model (DOM) document. cookie object. This helps prevent the cross-site scripting (XSS) attack.
To activate the HTTP security session management, execute Transaction SICF_SESSIONS. Select the ABAP client for which you want to activate the session, and click on the Activate icon, as shown in the following figure.
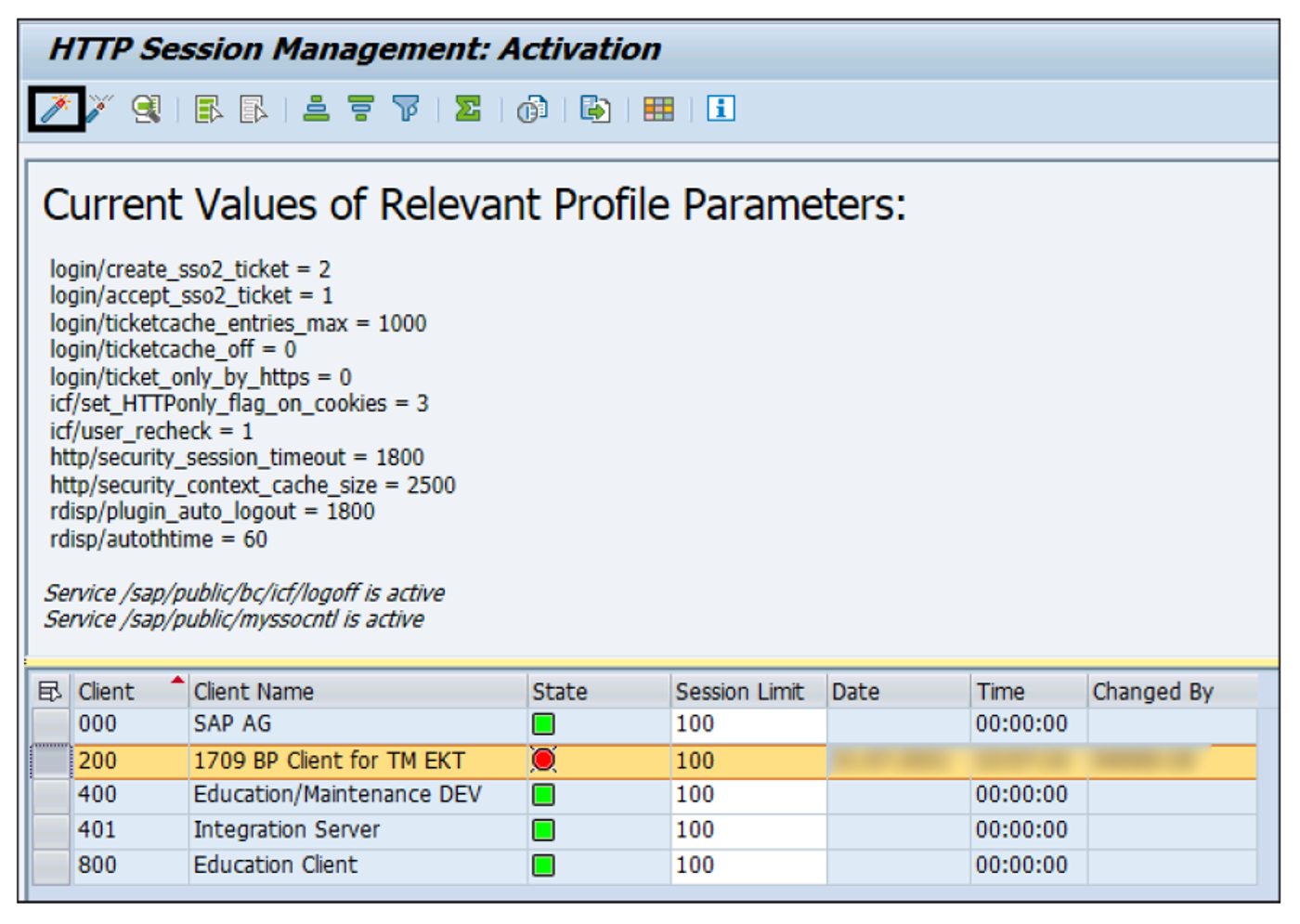
It’s important to maintain the relevant profile parameters for HTTP security session management. To maintain the profile parameters, execute Transaction RZ10. The current values of these profile parameters are also visible in Transaction SICF_SESSIONS, as shown above.
Some of the important profile parameters and their preferred values are as follows.
login/ticket_only_by_https
Generate a ticket that will only be sent via HTTPS. Possible values are as follows:
- 0: Cookie is always sent.
- 1: Cookie is sent by the browser only during the HTTPS connections. This is the preferred value.
icf/set_HTTPonly_flag_on_cookies
Set the HttpOnly flag for ICF cookies. Possible values are as follows:
- 0: HttpOnly attribute is active for all ICF cookies. This is the preferred value.
- 1: HttpOnly attribute is inactive for ICF logon cookie.
- 2: HttpOnly attribute is inactive for ICF cookies other than the ICF logon cookie.
- 3: HttpOnly attribute is inactive for all ICF cookies
login/create_sso2_ticket
Permit generation of single sign-on (SSO) tickets. The possible values are as follows:
- 0: No SSO ticket creation.
- 1: Create an SSO ticket including certificate.
- 2: Create an SSO ticket without certificate.
- 3: Generate only assertion tickets. This is the recommended value for session management.
login/accept_sso2_ticket
Permit/prevent logon with an SSO ticket. The possible values are as follows:
- 0: Logon with tickets isn’t permissible.
- 1: Logon with tickets is permissible. This is the preferred value.
login/ticketcache_off
Switch off caching for the SAP logon ticket. Possible values are as follows:
- 0: Caching activated. This is the preferred value.
- 1: Disable caching.
http/security_session_timeout
Timeout for HTTP security sessions. The default value is 1800 seconds.
http/security_context_cache_size
Size of the HTTP security session context cache. The default value is 2500. The possible value range is 500–250000.
login/ticketcache_entries_max
Maximum number of entries for the SAP logon ticket cache. Default value is 1000.
icf/user_recheck
Logon data check for HTTP queries for an existing HTTP session. This parameter is only relevant if security session management isn’t active. Possible values are 0 for not active and 1 for active.
rdisp/plugin_auto_logout
Specifies the maximum period of inactivity for the user context of an external plug-in (e.g., HTTP), before the system closes it. Default value is 1800 seconds.
rdisp/autothtime
Time cycle for periodic task handler checks. Defines the time interval between the checks performed periodically in the task handler, such as the automatic resetting of trace files, the checking of the context pool for RFC servers or external plug-ins (HTTP, etc.), and the automatic logon for external plug-ins (HTTP, etc.). Default value is 60 seconds.
Learn ABAP with Rheinwerk Courses!
Ready to level up your ABAP skills? Explore the full range of our ABAP-focused online courses, from foundational programming to advanced RAP, CDS, AMDP, unit testing, and more. Each one is instructor-led (live and on-demand), includes recordings and slide decks, and is designed to give you practical take-away skills you can apply right away in your SAP landscape. Click on the banner below to get started!
Editor’s note: This post has been adapted from a section of the e-book Implementing SAP Fiori 3 Security by Neha Gulati and Shreya Gulati.




Comments