Encrypting communications with SAP HANA is crucial. However, encryption can also be used to secure the data stored on the SAP HANA server’s persistent layers.
Although SAP HANA is an in-memory database, its data is not exclusively stored in-memory. SAP HANA will periodically create savepoints to mirror the in-memory data to disk. The savepoint process saves the data to the /hana/data/<SID> volume hosted on each SAP HANA server node.
In addition to these data savepoints, each committed transaction is simultaneously written to the /hana/log/<SID> volumes and memory on each SAP HANA server node. In the event of a power failure, the SAP HANA system will recreate the in-memory data using a combination of the persistent data snapshots stored in the /data volume and the transaction redo logs stored in the /log volume of each SAP HANA server node. Because these storage areas contain binary versions of the data hosted in SAP HANA, you should encrypt this data.
The same is true if you back up the database to a disk of an NFS location. In addition to data and log encryption, SAP HANA also support backup media encryption. Once enabled, the backup file will be encrypted with the same root keys used to encrypt the data and log partitions. Once enabled, the encrypted backup files cannot be restored or accessed with an SAP HANA database unless that database has the exact same root keys.
Users with access to the SAP HANA OS can potentially access unencrypted data hosted in the data or log volumes. Most organizations vigorously restrict access to the OS of on-premise implementations of SAP HANA, but organizations leveraging hosted or cloud-based SAP HANA implementations might have limited control over users with OS-level access or physical access to the storage drives. When access to the OS can’t be properly validated, we highly recommend that backup, data, and log volume encryption be used. The same is true when individuals with physical access to the disk drives aren’t properly managed.
Now, let’s review how SAP HANA manages the root keys used for encryption.
Server-Side Data Encryption
SAP HANA has a built-in encryption service to help you manage the encryption of data hosted in the data and log volumes. This service uses a secure store in the file system (SSFS) to protect the encryption root keys. Encryption root keys are the basis for all public or private keys used to encrypt data or communications within the SAP HANA system. SAP HANA has two SSFSs. The first SSFS is the SAP HANA instance SSFS, which protects the root keys used to encrypt information stored in the data and log volumes. The second SSFS is the system PKI SSFS, which protects root certificates used to secure internal communications.
The instance SSFS key is stored on the OS in the following location by default:
/usr/sap/<SID>/SYS/global/hdb/security/ssfs
Replace the <SID> variable in the example with the SID of your SAP HANA system.
Within the folder location, you’ll find two files: SSFS_<SID>.DAT and SSFS_<SID>.KEY. The system PKI SSFS key is stored on the OS in the following location by default:
/usr/sap/<SID>/SYS/global/security/rsecssfs/data
Replace the <SID> variable in the example with the SID of your SAP HANA system. Within the folder location, you’ll find two files: SSFS_<SID>.DAT and SSFS_<SID>.KEY.
Given their importance, these keys should be backed up and stored in a root key backup file. This backup file and its location must be accessible by the administrator during a recovery situation for a new SAP HANA host or a host with a new key generated after the backup file’s creation date. When data or log volume encryption is enabled, the SSFS will need to be restored from a backup prior to a database recovery. However, if you’re restoring a backup to the same SAP HANA database used to generate the backup files and the SSFS keys weren’t changed following the backup, SSFS key recovery is not necessary. The backup media can be restored because the SSFS on the target match the SSFS keys active during backup.
Next, we’ll provide more details about the processes used to back up and restore SSFS keys. Your organization must maintain backups of your SSFS keys each time they’re changed and prior to enabling backup, data, or log volume encryption. If you lose your SSFS keys and SAP HANA system, you won’t be able to recover the database to another SAP HANA instance.
Managing Root Keys within the SSFS
A unique root key is generated during the standard installation or upgrade of each SAP HANA instance. A standard installation is one in which a documented SAP HANA installation method is followed. However, because SAP HANA is often delivered as an appliance, the appliance vendor may have used a copy of the same encryption root keys within each of its appliance builds. For example, the vendor might deploy a copied image of the SAP HANA appliance’s file system. Using an image provides for the quick and consistent deployment of the SAP HANA software, but each default instance ends up using the same root keys and SSFSs. Organizations also must consider the security of the SSFS and its keys during installation. SAP HANA currently must be deployed by a certified vendor or certified individual. That individual could make a copy of the root keys and store them insecurely outside of the organization’s control. As a result, no guarantee can be made that a copy of the encryption root keys doesn’t exist outside the organization. These keys should therefore be changed after the vendor has completed the installation.
Therefore, often an organization will need to generate new encryption root keys following the initial deployment of the SAP HANA system. Starting with SAP HANA 2.0, when new root keys are generated, the SSFS should be backed up. To generate new keys, organizations can execute a series of SQL statements. To perform a backup of the SSFS, command line access to the operating system is required. The process used to generate new root keys in SAP HANA 2.0 is as follows:
- Generate new root keys using SQL commands.
- Back up the new keys and store them in a secure file location.
- Activate the new keys using SQL commands.
To properly perform these activities, grantees will need the <sid>adm operating system credentials to execute the command line utility hdbnsutil. The grantee will need the ENCRYPTION ROOT KEY ADMIN system privilege. You also need to establish a password for the root key backup file. To establish this password, execute the following SQL statement:
ALTER SYSTEM SET ENCRYPTION ROOT KEYS BACKUP PASSWORD "<Password>";
To generate new root keys for the SAP HANA data volume, execute the following SQL command:
ALTER SYSTEM PERSISTENCE ENCRYPTION CREATE NEW ROOT KEY WITHOUT ACTIVATE;
To generate new root keys for the SAP HANA log volume, execute the following SQL command:
ALTER SYSTEM LOG ENCRYPTION CREATE NEW ROOT KEY WITHOUT ACTIVATE;
To generate new root keys for SAP HANA’s internal application encryption, execute the following SQL command:
ALTER SYSTEM APPLICATION ENCRYPTION CREATE NEW ROOT KEY WITHOUT ACTIVATE;
With all three of these SQL statements, notice that the WITHOUT ACTIVATE option was specified. This option allows new keys to be generated without making them active within the system. You must back up the root keys prior to their activation but just after their creation. To do so, you can use the hdbnsutil command line utility. To use this utility, log on to the SAP HANA operating system with the <sid>adm credentials. Alternately, you can execute a SQL statement that returns a CLOB field containing an encrypted text message. You can copy the text message to a file and save it with the .rkb extension.
To use the hdbnsutil command line utility, log on to the SAP HANA system using your Secure Shell (SSH) service of choice. Log on to the shell using the <sid>adm credentials. This utility is stored in /usr/sap/<sid>/HDB<instance_number>/exe. Execute the following command to back up the root keys:
./hdbnsutil -backupRootKeys <file path and name>.rkb --dbid=<dbid> --type='ALL'
If SAP HANA is a single-container system, you can omit the –dbid=<dbid> portion of the command. The variable <dbid> should be replaced with the tenant database ID. If you don’t have access to the operating system shell, you can also execute a SQL statement to return a CLOB field containing the contents of the RKB file. Copy and save the contents of the CLOB field to a file with the .rkb extension. To return the CLOB field, execute the following SQL:
SELECT ENCRYPTION_ROOT_KEYS_EXTRACT_KEYS
('PERSISTENCE, APPLICATION, LOG') FROM DUMMY
Before activating the new root keys, you must validate that you have the correct password required to restore the root keys. To do so, execute the following command from the SAP HANA OS shell:
./hdbnsutil -validateRootKeysBackup <path to filename> --password="<password>"
When a backup is created with data and log volume encryption enabled, that backup can only be restored to a system with the same SSFS and root keys. If you need to restore a backup to a system with different root keys, you must first restore the root keys from the RKB file. To recover root keys, execute the following command from the operating system shell; you must be authenticated as the <sid>adm user to restore the root keys:
./hdbnsutil -recoverRootKeys <path to filename>.rkb --dbid=<dbid>
--password="<password>" --type=ALL
If SAP HANA is a single-container system, you can omit the –dbid=<dbid> portion of the command. The variable <dbid> should be replaced with the tenant database ID.
Once the backup file is generated and validated, you can activate the new keys within the system. To activate the keys for all three areas, execute the following three statements:
ALTER SYSTEM PERSISTENCE ENCRYPTION ACTIVATE NEW ROOT KEY;
ALTER SYSTEM LOG ENCRYPTION ACTIVATE NEW ROOT KEY;
ALTER SYSTEM APPLICATION ENCRYPTION ACTIVATE NEW ROOT KEY;
To view the current and historical status of root keys generated within the system, query the ENCRYPTION_ROOT_KEYS system view. To query this view, execute the following SQL statement from the SQL console:
SELECT * FROM SYS.ENCRYPTION_ROOT_KEYS;
You can also use the SAP HANA cockpit to manage your SSFS keys. Once you’re connected to a database within the SAP HANA cockpit, from the System Overview page, click the Data Encryption tile to manage your SSFS keys. Again, click the Data Encryption link to access the Data Encryption Configuration management interface. Locate the Data at Rest Encryption section, as shown below, to view the current status of Data Volume Encryption and Log Volume Encryption. You can also use this page to enable or disable encryption.
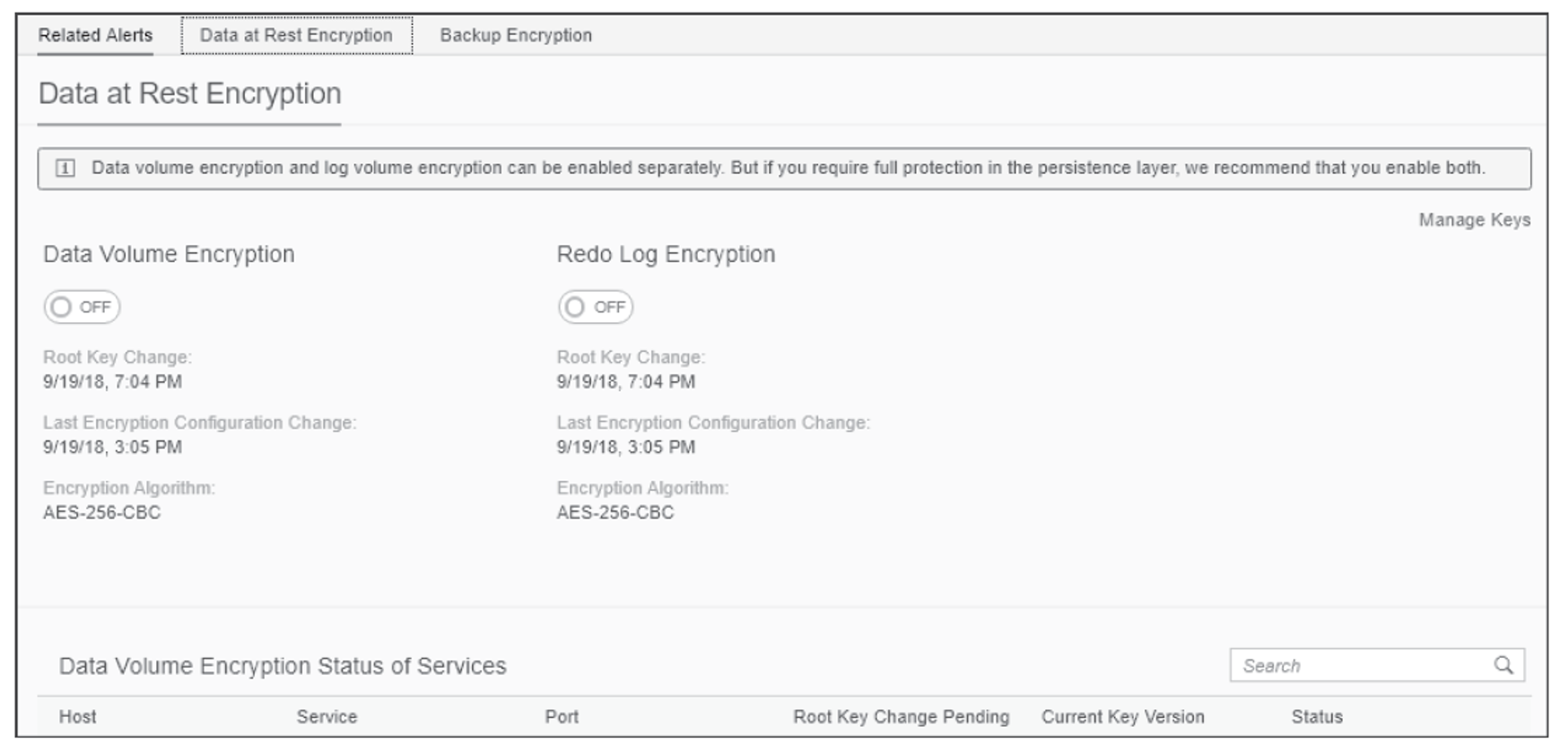
On the right side of the Data Volume Encryption section, as shown in the next figure, you’ll notice the Manage Keys link. Click the link to access the Manage Keys interface. In this interface, you can Change Root Key Backup Password, Back Up Root Keys, Generate Root Keys, and view the history and status of the root keys. A history is maintained for Data Volume Encryption Root Keys, Redo Log Encryption Root Keys, and Backup Encryption Root Keys. Click the See All Versions link to view the history of each key.
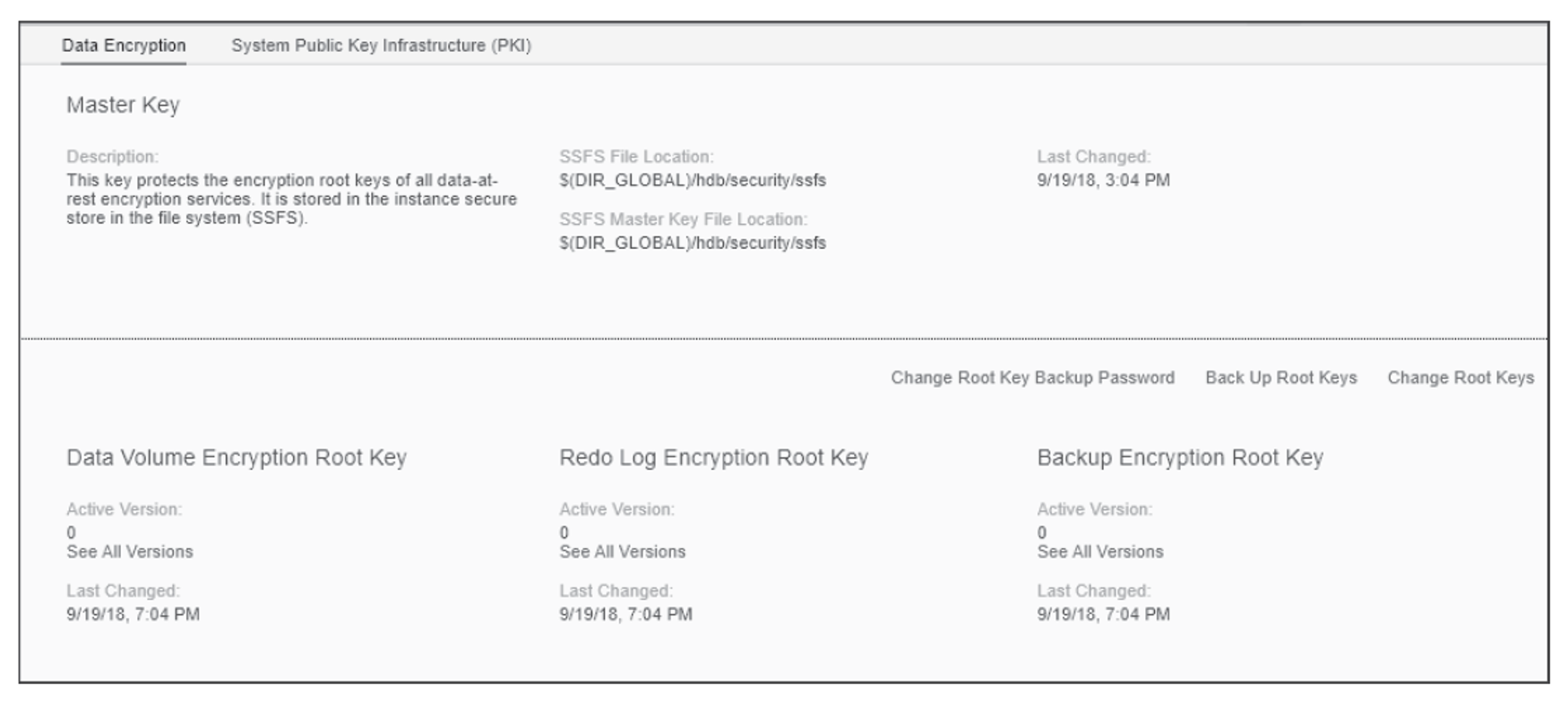
As the name of the link implies, use the Change Root Key Backup Password link to access a popup window where you can change the password. Remember this password since it’s required to restore the SSFS keys prior to restoring an encrypted backup.
Click the Backup Encryption Root Keys link to download a backup of the root keys. This backup is useful in situations where you need the backup files but don’t have OS-level access. Remember to save the keys so that they can be restored before also restoring any encrypted backup media. The restore to any target SAP HANA system will fail if the SSFS keys in the target do not match the keys used when the backup media was created.
The Change Root Key Backup Password link will launch a three-step wizard to walk you thought changing or regenerating new SSFS keys. Once you have changed the SSFS keys, remember to make a new backup of the keys.
Generating new root keys within the SSFS is an important step that all organizations should consider after receiving a new SAP HANA appliance. In the next sections, we’ll explore the requirements and commands necessary to enable data and log volume encryption.
Encrypting the Data Volume
Two main ways exist for enabling data volume encryption in SAP HANA 2.0: via a specialized SQL statement or via the Data Encryption link in the SAP HANA cockpit.
Using SQL
Note that, in older versions of SAP HANA, you can’t enable data volume encryption if extended storage has already been enabled within the system; you’ll need to move extended storage tables back to in-memory storage and disable extended storage prior to executing the command successfully. Users will also need the ENCRYPTION ROOT KEY ADMIN system privilege to enable/disable data volume encryption in all versions of SAP HANA. To enable data volume encryption, execute the following SQL command:
ALTER SYSTEM PERSISTENCE ENCRYPTION ON;
To monitor the status of data volume encryption, execute the following SQL statement:
SELECT * FROM SYS.M_ENCRYPTION_OVERVIEW
Using the SAP HANA Cockpit
You can also use the SAP HANA cockpit to manage data volume encryption. Once you’re connected to a database within the SAP HANA cockpit, from the System Overview page, click the Data Encryption tile to manage you SSFS keys and enable or disable encryption. The same tile also includes a section where you can quickly enable or disable data volume encryption by using the On/Off slider. You can also access this same option by clicking the Data Encryption link. Locate the Data at Rest Encryption section to view the current status of Data Volume Encryption and Log Volume Encryption or to use the On/Off slider to disable or enable encryption, as shown in the next figure. Below the slider is also metadata that will indicate the last time the keys were changed and the algorithm used for the encryption.
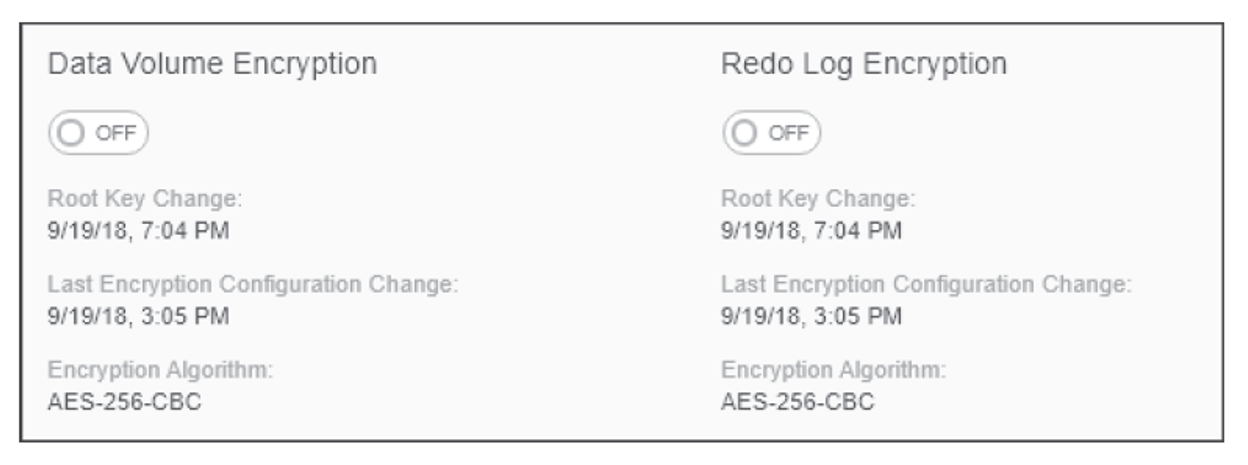
Encrypting the Log Volume
Encrypting the log volume is a feature that was first made available in SAP HANA 2.0 SPS 00. Log volume encryption can be enabled using SQL and using the SAP HANA cockpit.
Using SQL
You can use SQL from any supported SQL console to enable redo log volume encryption. To enable log volume encryption, execute the following SQL command:
ALTER SYSTEM LOG ENCRYPTION ON;
To monitor the status of log volume encryption, execute the following SQL statement:
SELECT * FROM SYS.M_ENCRYPTION_OVERVIEW
Using the SAP HANA Cockpit
The SAP HANA cockpit can also be utilized to enable or disable redo log volume encryption. From the System Overview page, click the Data Encryption tile to manage your SSFS keys and enable or disable encryption. The same tile also includes a section where you can quickly enable or disable redo log volume encryption by using the On/Off slider. You can also access this same option by clicking the Data Encryption link. Locate the Data at Rest Encryption section to view the current status of Log Volume Encryption. Use the On/Off slider to disable or enable redo log volume encryption
Encryption the Backup Media
Encrypting the backup media is a feature that was first made available in SAP HANA 2.0 SPS 01. Backup encryption can be enabled using SQL and using the SAP HANA cockpit.
Using SQL
You can use SQL from any supported SQL console to enable redo log volume encryption. To enable backup encryption, execute the following SQL command:
ALTER SYSTEM BACKUP ENCRYPTION ON;
To monitor the status of backup encryption, execute the following SQL statement:
SELECT * FROM SYS.M_ENCRYPTION_OVERVIEW
Using the SAP HANA Cockpit
The SAP HANA cockpit can also be utilized to enable or disable backup encryption. From the System Overview page, click the Data Encryption tile to manage your SSFS keys and enable or disable encryption. The same tile also includes a section where you can quickly enable or disable backup encryption by using the On/Off slider. You can also access this same option by clicking the Data Encryption link. Locate the Backup Encryption section to view its current status, as shown below. Again, use the On/Off slider to disable or enable backup encryption.
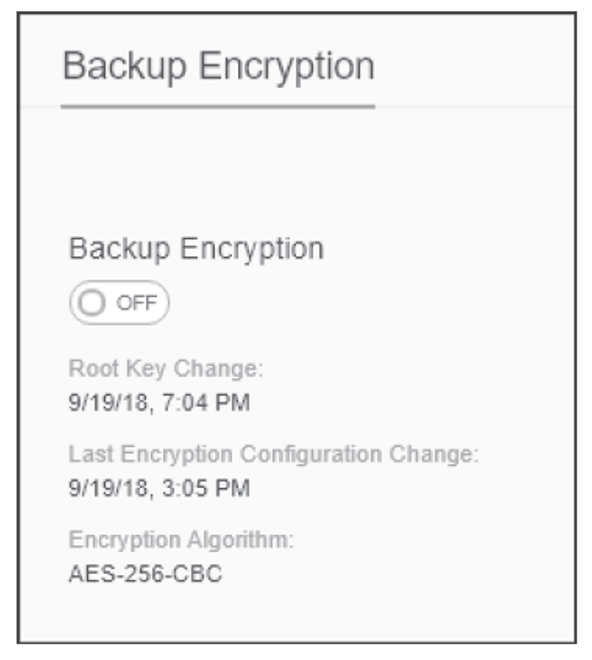
Conclusion
You now have a better understanding of encrypting data with SAP HANA. Time to secure your valuable information; this will help you both from an SAP HANA security standpoint but also give you practical knowledge to use when taking the SAP HANA Application Associate Certification Exam.
Editor’s note: This post has been adapted from a section of the book SAP HANA 2.0 Security Guide by Jonathan Haun.



Comments