Five key capabilities are enabled by SAP Access Control. This blog post provides a detailed description of these capabilities and how they benefit an organization.
The figure below shows these capabilities.
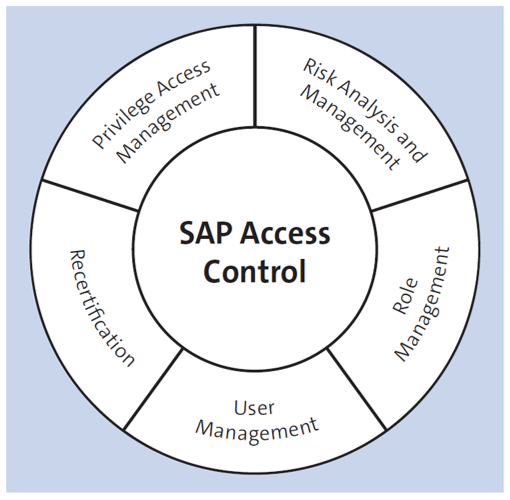
Key Capabilities
The primary purpose of SAP Access Control, as mentioned earlier, is to ensure that your organization can adhere to compliance requirements. Three phases are followed in the implementation of SAP Access Control.
Get Clean
Get clean begins with identifying the existing risks. SAP Access Control’s risk analysis and management features identify SoD and critical risks. Further, business teams are responsible for adjusting their processes to reduce potential risks.
Stay Clean
Once risks have been mitigated and remedied, your enterprise must maintain clean systems, which is referred to as “stay clean.” This goal can be achieved through business role management, user provisioning, and privilege management.
Stay in Control
To keep the system clean, periodic reviews of user access, SoD, and firefighter IDs (FFIDs) can be conducted. The process is referred to as compliance recertification.
The table below lists the SAP Access Control components used during each phase.

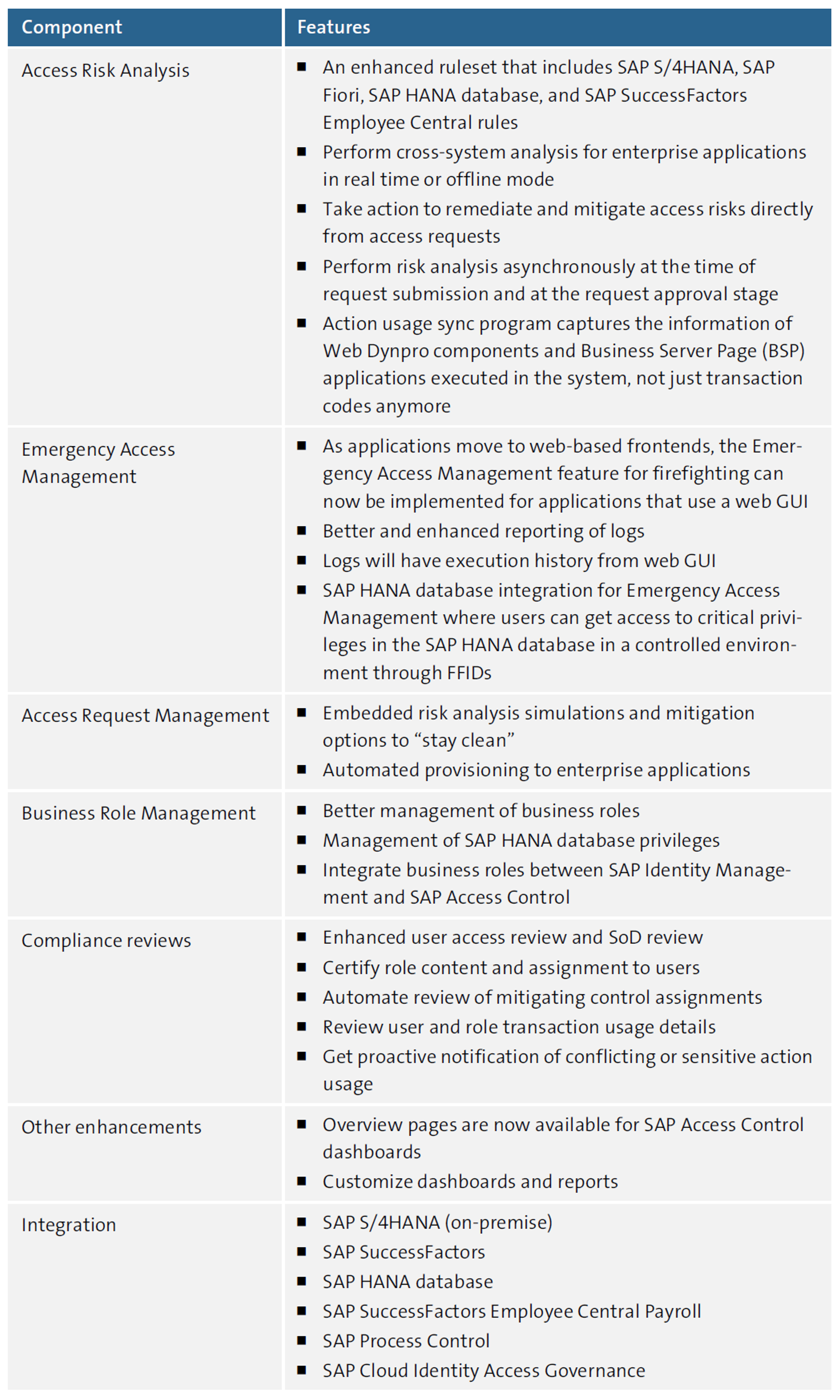
The next table lists some new features that SAP Access Control 12.0 offers in addition to its standard features.
Supported Systems
SAP Access Control can be integrated with all SAP NetWeaver systems, as mentioned in Section 1.3.1. To utilize the various components, you must install the GRCPINW plug-in (SAP NetWeaver plug-in for SAP GRC solutions). As of version 12.0, SAP Access Control supports both v1100 and v1200, but not v1000.
RFC connections can be established once the plug-ins are installed.
Additionally, SAP Access Control 12.0 supports HR integration with SAP ERP and SAP S/4HANA for configuring HR triggers. To use this feature of SAP Access Control, the GRCPIERP plug-in must also be installed.
SAP Access Control 12.0 also supports SAP Identity Management and non-SAP identity management applications, which you can integrate with web services. Cloud applications like SAP Ariba, SAP Concur, and SAP SuccessFactors Employee Central can be connected using SAP Cloud Identity Access Governance/SAP Business Technology Platform (SAP BTP) cloud connectors.
When an application lacks a standard connector or integration capability, Pathlock adapters can be used.
Editor’s note: This post has been adapted from a section of the book SAP Access Control: The Comprehensive Guide by Raghu Boddu.



Comments