In this blog post, you’ll learn how to log on to the cloud connector itself. Depending on the roles you have, you can access different functions in the cloud connector.
After installing the cloud connector, the solution uses a file-based user store. Users are stored in the users.xml file in the config subdirectory of the cloud connector. Passwords are encrypted with a keystore certificate located in the same directory.
This file-based authentication is sufficient for smaller cloud connector installations. However, for larger installations, we recommend that you integrate file-based authentication with your company’s LDAP directory. With LDAP authentication, users are authenticated against your company’s LDAP directory service.
The following roles can then be assigned to users authenticated in this way:
- sccadmin: This role has full administrative rights in the cloud connector.
- sccdisplay: This role enables the display of all data in the cloud connector.
- sccsupport: This role is used to display data and support activities (e.g., to activate traces).
- sccmonitoring: This role is required to access the monitoring APIs of the cloud connector.
These roles can be used to differentiate between users who are only allowed to view the configuration and those who are responsible for the administration functions.
To switch from file-based authentication to LDAP-based authentication, follow these steps:
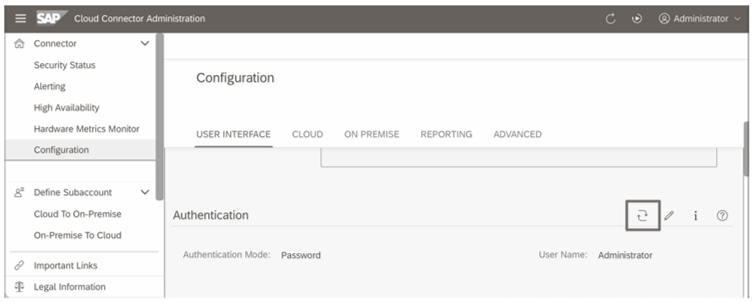
- On the cloud connector administration console, navigate to Connector > Configuration.
- Under the USER INTERFACE tab, switch to the Authentication
- To update the authentication method, click the icon, as shown in the figure below.
- A configuration dialog box opens where you can set the parameters for LDAP authentication. Maintain the Host field and other credentials for your connection. Select the Secure Host option to use the Lightweight Directory Access Protocol over SSL (LDAPS)
- In the Configuration field, enter the rest of the LDAP configuration, namely, the default user path and search pattern (userBase and userSearch) and the group path including search pattern (roleBase and roleSearch), as shown here.
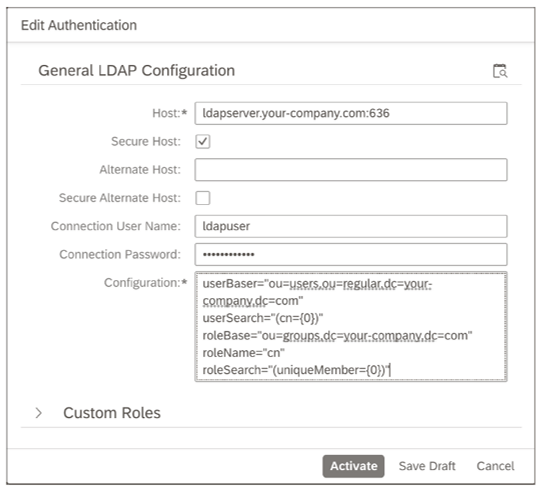
- Use the Test LDAP Configuration icon in the upper-right corner to test your settings. We recommend clicking this icon before saving the configuration.
- Activate the LDAP authentication via the Activate
Note: Do Not Use Talking User Accounts! If the user data of your LDAP directory is used via the cloud connector for authentication to SAP BTP, you must consider some security aspects. Do not use prefixes or suffixes to indicate users who have administrative access to systems in the cloud as administration users. For example, if you use a user name with the scheme <user>ADM for the configuration of your local Windows servers, you should not use this scheme in the cloud. Otherwise, attacks from the Internet could target these accounts specifically. If a user named MA00019 could be both an employee with the personnel number 19 and an employee with the name abbreviation MA, identifying these accounts as administration users for a brute force attack is already more difficult. If you use corresponding user names, you might consider providing only the users path of the LDAP directory for LDAP authentication and not providing the administrators branch for the cloud.
To turn LDAP authentication off again, the useFileUserStore file is available in the cloud connector directory. This file ensures that the system sets the authentication back to file-based authentication when the file is found, even though you may have previously switched to LDAP authentication. In production systems, we therefore recommend that you delete this file after enabling LDAP authentication or set it as non-executable.
Editor’s note: This post has been adapted from a section of the book Security and Authorizations for SAP Business Technology Platform by Martin Koch and Siegfried Zeilinger.



Comments